VPNs vs. Zero Trust: Which Is Right for Your Business?

Remote work, cloud services, mobile devices, and OT/ICS systems have transformed the way businesses access their resources. The traditional “castle‑and‑moat” network perimeter model is no longer sufficient. Now, more than ever, organisations must ask: Which access model fits our needs -a traditional VPN or a modern Zero Trust Network Access (ZTNA) framework?
At CyberSec Magazine, we’ll explore the background of VPNs and Zero Trust, compare their strengths and weaknesses (especially in IT, OT/ICS, and IIoT settings), and provide a structured guide to help you decide which access strategy is right for your business in 2025 -and how you might transition or integrate both models.
Background: From VPNs to Zero Trust
The Rise and Role of VPNs
A Virtual Private Network (VPN) creates an encrypted tunnel between a remote user/device and a private network. This allows remote workers to appear as if they are inside the corporate network, gaining access to internal resources.
VPNs served well in an era when users were few, applications were on‑premises, and networks were relatively static. However, they operate on a perimeter‑based trust model: once authenticated, the user often gains broad network access -sometimes more than needed.
Why the Assumptions Behind VPNs Are Challenged Today
Several forces are eroding the traditional VPN model:
- Hybrid and remote workforce: Connectivity from home, mobile devices, and edge sites is standard.
- Cloud and SaaS adoption: Applications no longer sit purely on‑premises, making central VPN tunnels inefficient and sometimes unnecessary.
- IT/OT convergence & IIoT: Industrial networks now link to IT, increasing exposure and diverging device types.
- Evolving threats: Adversaries exploit implicit trust, lateral movement, unmanaged devices, and remote vendor access.
As articulated in industry commentary, VPNs grant network‑level access but don’t always enforce least privilege or continuous verification.
Enter Zero Trust and ZTNA
The Zero Trust Architecture (ZTA) model assumes no user or device is trusted by default -internal or external. Every access request must be authenticated, authorised, and continuously verified.
Within this paradigm, Zero Trust Network Access (ZTNA) is the modern approach for remote access: instead of granting broad network access, it gives users access only to the specific applications or services they need, based on device posture, identity, context, and risk.
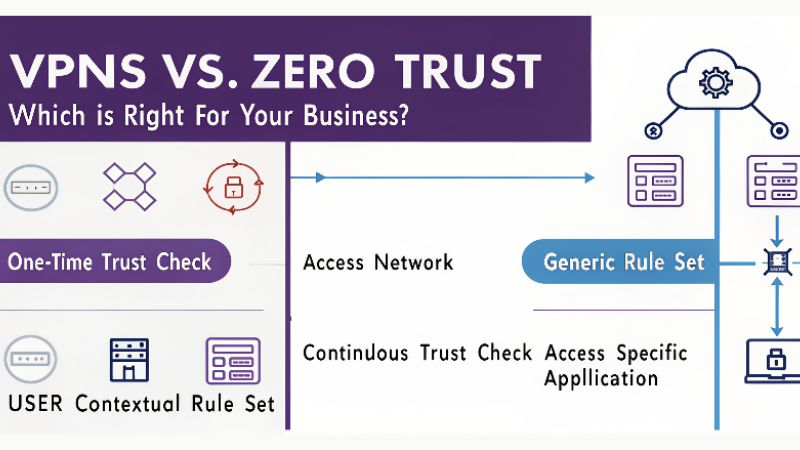
In short: VPNs provide network‑level tunnel access; ZTNA provides application‑level, context‑aware, least‑privilege access.
VPN vs. ZTNA: Key Differences
Here’s a breakdown of how the two models contrast in today’s environment:
| Feature | VPN | ZTNA / Zero Trust Network Access |
| Access Scope | Network‑level: once connected, access often spans large network segments. | Application‑level: access to specific services, based on context, device, user, and policy. |
| Trust Model | “Trust once connected” -user/device gets broad access. | “Never trust, always verify” -continuous checks, least privilege enforced. |
| Device & Posture Checks | Often minimal; focus is on tunnel establishment. | Strong device posture, identity, context validation before granting access. |
| Internal Movement Risk | Higher -once inside, adversaries can move laterally more easily. | Lower -segmentation, micro‑segmentation, application isolation reduce lateral movement. |
| Scalability & User Experience | Can become a bottleneck; back‑haul traffic; complex management. | Typically more scalable, better user experience, cloud‑friendly. |
| Best Fit (in general) | Smaller organisations, simpler remote access needs, legacy setups. | Modern, distributed, hybrid cloud/IT/OT/IoT environments with high security and dynamic access needs. |
Which One Is Right for Your Business? A Decision Framework
Choosing between VPN and ZTNA (or co‑existing models) depends on your business context, technology estate, security posture, and future roadmap. Here’s a step‑by‑step approach.
Step 1: Understand Your Access Use‑Cases
Ask:
- Who needs remote access? Employees, contractors, vendors?
- What resources are accessed? On‑prem servers? Cloud apps? OT/ICS systems?
- How many users, devices, locations? Are the devices managed or unmanaged?
- Do you support BYOD, IoT/IIoT, field engineers, remote plants?
If your access model is simple (few users, a well‑controlled network, legacy environment), a modern VPN solution may suffice. If you support hybrid/remote work, cloud apps, IT/OT convergence, unmanaged devices, or vendor access -then ZTNA is likely more appropriate.
Step 2: Assess Your Risk & Threat Landscape
Some key questions:
- Is lateral movement a real threat in your environment (especially if IT/OT converge)?
- Do you have unmanaged/field devices, remote vendors, BYOD, or edge sites?
- Are resources distributed across on‑prem and multi‑cloud environments?
- Do compliance or industrial‑control regulations demand granular access, excellent logging, micro‑segmentation?
If risk is high, the broader attack surface, or operations include OT/ICS, then ZTNA offers stronger control.
Step 3: Evaluate Existing Infrastructure & Constraints
- Do you already have a VPN infrastructure? Are users manageable in numbers?
- How old are your systems, do you have legacy OT/ICS endpoints that may not support modern agents?
- What is your network topology, and how well segmented are IT and OT?
- What is your user‑experience requirement (latency, remote access to cloud apps vs internal apps)?
In many environments, VPNs continue to serve legacy needs or simple use‑cases, while ZTNA is introduced for new use‑cases.
Step 4: Choose Implementation Approach
- VPN‑only strategy: Acceptable for small businesses, limited remote users, simple infrastructure. Lower cost, familiar.
- ZTNA‑only strategy: Makes sense for cloud‑first, hybrid workforce, strong security posture, modern application access. Requires investment, maturity, and change‑management.
- Hybrid strategy: Many organisations adopt both -maintaining VPN for legacy systems/OT endpoints while introducing ZTNA for cloud apps, remote employees, vendor access. This phased approach allows a smoother transition.
Step 5: Link to OT/ICS and Industrial Considerations
For organisations with industrial control systems, OT/IoT, remote engineers, or multiple field sites -additional factors apply:
- Vendor/contractor remote access: ZTNA strongly limits access to only required systems and supports session logging/recording.
- Legacy OT endpoints: Some may not support modern clients. VPN may work but with compensating controls (segmentation, monitoring).
- Availability/safety: Remote access must not interfere with operational continuity; controls must respect OT constraints (e.g., no heavy scanning, low latency).
- Cross‑domain (IT→OT) lateral movement risk is higher; ZTNA’s micro‑segmentation and application isolation help reduce the blast radius.
Advantages & Limitations: A Balanced View
Benefits of VPNs
- Established, well‑understood technology; many IT teams are familiar with it.
- Strong encryption in transit for remote users and basic security on untrusted networks.
- Often lower initial cost for small scale use‑cases, few remote users.
- May integrate well with legacy systems, older remote sites and simpler setups.
Limitations of VPNs
- Grant broad access once connected -violating the least‑privilege principle.
- Scalability and performance issues: back‑hauling traffic, latency for cloud apps.
- Minimal continuous verification of device posture; unmanaged or compromised devices can become entry points.
- Less visibility and control over application‑level access; more risk of lateral movement.
Benefits of ZTNA / Zero Trust
- Granular, context‑aware access: users/devices get only what they need when they need it.
- Reduced attack surface: internal networks are hidden, access is limited.
- Better suited to cloud, hybrid workforce, and BYOD/remote scenarios.
- Better lifecycle control: continuous re‑verification, device posture checks, adaptive policies.
Limitations of ZTNA
- Implementation complexity: requires identity management, device posture, continuous monitoring, often cultural change.
- Legacy system support: older applications or devices may not integrate easily into ZTNA model; might need exceptions or hybrid architecture.
- Cost and maturity: although matured, many organisations still face learning curves, tool integration, and staff training.
- Transition challenges: moving from VPN‑centric to ZTNA‑centric access may require phased approach and change in network architecture.
Practical Implementation: Transitioning from VPN to Zero Trust
Here’s a practical roadmap your organisation can follow to adopt or move toward ZTNA while managing existing VPN infrastructure.
Phase 1: Inventory & Assessment
- Identify all remote access points: home offices, public WiFi, mobile, branch/edge sites, field engineers, vendor access.
- Identify resources accessed: enterprise applications, OT/ICS systems, vendor jump hosts.
- Inventory devices: corporate, BYOD, unmanaged, legacy OT equipment.
- Assess network segmentation, internal trust zones, remote‑access topology and risk (especially IT → OT).
Phase 2: Immediate Optimisation of Existing VPN
- For legacy VPN users, enforce stronger access controls: MFA, device posture checks, segmentation of VPN users into dedicated access zones.
- Review VPN logging, visibility and monitoring; ensure remote sessions are logged and audited.
- Segment access: even via VPN, restrict users to minimal resources rather than full network.
- For remote OT/ICS access, build dedicated vendor‑access gateways, jump hosts; reduce risk of broad network access.
Phase 3: Pilot ZTNA for Select Use‑Cases
- Choose a manageable pilot: e.g., remote employees accessing cloud or SaaS apps, field engineers needing specific applications.
- Deploy ZTNA solution: identity/authentication, device posture, context checks, micro‑segmentation.
- Configure application‑level access: users/devices get direct access to apps, network remains hidden.
- Monitor performance, user experience and security outcomes.
Phase 4: Expand ZTNA and Re‑Architect Access
- Extend ZTNA coverage to larger user base, vendor sessions, remote sites, hybrid/edge environments.
- Begin phasing out segments of VPN access where possible.
- Align with Secure Access Service Edge (SASE) architecture: integrate network access, security controls, cloud access in unified model.
- For OT/ICS environments, ensure ZTNA supports vendor/contractor sessions, jump hosts, field devices, segmentation of control networks.
Phase 5: Continuous Review, Monitoring and Governance
- Monitor KPIs: incidents from remote access, user experience metrics, mean time to detect lateral movement, number of segmented sessions.
- Regularly review access policies, device posture rules, segmentation strategy, legacy system exceptions.
- Train users, enforce change management and refine architecture.
- Maintain VPN infrastructure only where needed (legacy systems, temporary fallback) and treat it as part of hybrid strategy rather than default.
Conclusion: Which Should You Choose -or Both?
The short answer: It depends. But in 2025, with modern distributed workforces, cloud applications, remote access needs, and IT/OT convergence, the balance is shifting clearly toward Zero Trust/ZTNA for many organisations.
If your business is still reliant on legacy remote access, smallscale remote users and primarily on‑prem applications, a well‑managed VPN may still suffice. But if you support remote/hybrid workforces, BYOD, vendor/contractor access, cloud/OT integration or need stronger security controls -then ZTNA is likely the more future‑proof choice.
Key take‑aways
- VPNs remain relevant in certain legacy or simple use‑cases—but they are no longer a one‑size‑fits‑all remote access solution.
- ZTNA/Zero Trust brings least privilege, context‑aware access, reduced attack surface and better fit for modern architectures.
- Many organisations will adopt a hybrid approach: keep VPN for legacy or limited access cases, adopt ZTNA for critical, modern access needs.
- For OT/ICS environments, vendor access, legacy endpoints and remote/edge sites complicate matters -ZTNA helps but must be integrated carefully respecting operational constraints.
- Transition thoughtfully: inventory your users/resources/devices, optimise VPN in the short term, pilot ZTNA, expand, and monitor continuously.
- Ultimately, remote access strategy is a business decision, not purely technical: align access model with risk tolerance, regulatory needs, workforce model and technology roadmap.
At CyberSec Magazine, we believe the future of secure access lies in adaptability, context, segmentation, and least‑privilege -not treating every connection as trusted once inside the tunnel. If your organisation is exploring access strategy for 2025 and beyond, we’d encourage you to benchmark your current model, map your users/devices/applications, and begin the transition toward a Zero Trust‑centric architecture.
