Remote Access in Industrial Environments: Risks and Solutions

In the era of Industry 4.0, remote access has become indispensable for industrial operations. It enables engineers, technicians, and vendors to monitor systems, perform maintenance, and troubleshoot issues without being physically present. While this connectivity enhances efficiency and reduces downtime, it also introduces significant cybersecurity risks. Industrial Control Systems (ICS) and Operational Technology (OT) networks, traditionally isolated, are now more interconnected, making them attractive targets for cyberattacks.
This article delves into the risks associated with remote access in industrial environments and outlines effective solutions to mitigate these threats.
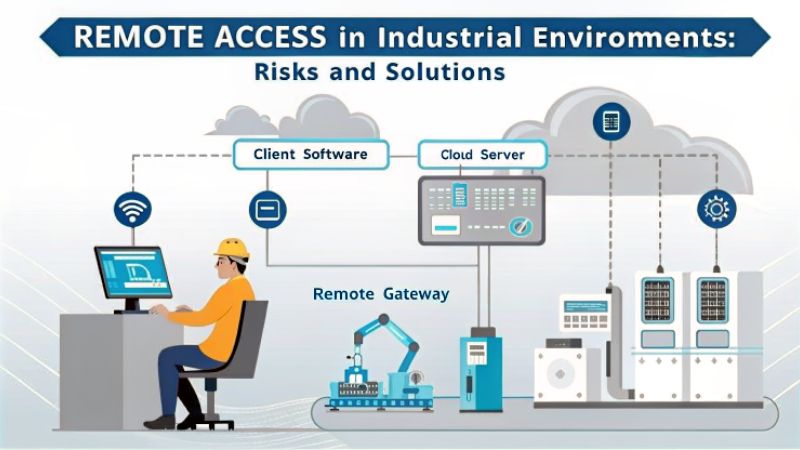
Understanding the Risks of Remote Access
1. Increased Attack Surface
Remote access inherently expands the attack surface of industrial networks. Exposed systems, such as SCADA, PLCs, and HMIs, are vulnerable to unauthorized access if not properly secured. A recent report highlighted that over 200,000 industrial systems were exposed to the internet, many lacking basic authentication and carrying severe vulnerabilities .
2. Legacy Systems Vulnerabilities
Many OT systems are built on legacy infrastructure that lacks modern security features. These systems often run outdated software, making them susceptible to known exploits. For instance, malware like LogicLocker has targeted PLCs by exploiting weak authentication mechanisms .
3. Third-Party Access Risks
Vendors and contractors often require remote access to perform maintenance or updates. Without stringent controls, this can lead to unauthorized access or misuse. Implementing Just-In-Time (JIT) access and Privileged Access Management (PAM) can help mitigate these risks .
4. Lack of Visibility and Monitoring
Without continuous monitoring, unauthorized access or anomalous activities can go undetected. Implementing Security Information and Event Management (SIEM) systems tailored for OT environments can provide real-time visibility and alerting .
Best Practices for Securing Remote Access
1. Implement Zero Trust Architecture
Adopt a Zero Trust model, which assumes that threats could be internal or external. This approach requires strict verification for every user and device attempting to access the network, regardless of their location.
2. Use Secure Remote Access Solutions
Deploy remote access solutions designed for OT environments. These solutions should offer encrypted communication, strong authentication mechanisms, and the ability to monitor and control access in real-time. Platforms like Waterfall’s HERA provide zero-trust, reliable remote access for critical industrial operations .
3. Network Segmentation and Micro-Segmentation
Segment OT networks from IT networks and further divide them into smaller zones. This limits lateral movement in case of a breach and confines potential damage to isolated segments .
4. Enforce Strong Authentication and Access Controls
Implement Multi-Factor Authentication (MFA) and enforce the principle of least privilege. Ensure that users have access only to the resources necessary for their roles and that all access is logged and monitored.
5. Regularly Update and Patch Systems
Establish a routine for updating and patching OT systems. This includes applying security patches to both hardware and software components to protect against known vulnerabilities.
6. Conduct Security Awareness Training
Educate personnel about the risks associated with remote access and best practices for maintaining security. Regular training can help prevent human errors that lead to security breaches .
Case Studies and Real-World Applications
Case Study 1: Securing Remote Access in a Water Treatment Facility
A municipal water treatment facility faced challenges with remote access for maintenance personnel. By implementing a secure remote access solution with MFA and network segmentation, the facility was able to reduce unauthorized access attempts by 80% and improve response times to incidents.
Case Study 2: Protecting Manufacturing Operations
A manufacturing plant integrated a Zero Trust model and PAM to manage third-party vendor access. This approach led to a 50% decrease in security incidents related to vendor access and enhanced overall system reliability.
Conclusion
Remote access is essential for the efficient operation of modern industrial environments. However, without proper security measures, it can expose critical systems to significant risks. By implementing best practices such as Zero Trust architecture, secure remote access solutions, network segmentation, and continuous monitoring, organizations can mitigate these risks and ensure the integrity and availability of their OT networks.
For more insights into securing remote access in industrial environments, visit.
